In the computer age, where attempted intrusions are as common as changing weather, safeguarding your network is of the utmost importance. Uncomplicated Firewall (UFW) is a user-friendly interface designed to facilitate the management of your firewall on Ubuntu servers. Acting as the guardian at the gate, UFW controls who gets in and out of your system’s network.
UFW simplifies the complexities of network traffic management with intuitive commands, making security accessible for users at all skill levels. UFW serves as a robust framework for managing iptables, which control the network packet filter rules in the Linux kernel. By the end of this guide, you’ll be skillfully wielding UFW, ensuring your Ubuntu server stands fortified against any unwanted intrusions.
As we embark on this journey of tightening your digital defenses, keep in mind that configuring your firewall should not be complicated. With UFW, you’re just a few commands away from achieving a shielded network.
Understanding Firewalls and UFW
Imagine a firewall as the ultimate guardian of your computer’s network traffic. It’s your frontline defense, meticulously scrutinizing data packets to determine whether to let them through or block them by setting up rules that define which services are accessible and from where a firewall plays a critical role in your system’s security apparatus.
Now, let’s introduce UFW—Uncomplicated Firewall. Built with simplicity in mind, UFW is an interface streamlining firewall management. This reliable tool converts your security protocols into iptables rules with no need to delve into the complex syntax.
But what makes UFW special? above all, it’s user-friendly. Whether running a perso nal blog or managing a fleet of servers, UFW is designed to make your life easier. It’s packaged with sensible defaults and a straightforward way to set up sophisticated rules, which means you don’t require extensive knowledge on security to use it effectively.
UFW is not only easily accessible but also highly powerful. It enables you to customize your firewall. Whether you’re opening a single port for a web server, blocking all incoming traffic, or even managing complex networking scenarios, UFW has got you covered.
In the following sections, we’ll explore the potential of UFW together, ensuring that your Ubuntu server is not just running but running securely. From installation to rule management, you’ll learn how to wield this tool confidently, protecting your system from the unknown dangers of the internet.
With UFW, simplicity does not come at the expense of functionality. Let’s move forward and see how this guardian equips you with the necessary tools to ward off cyber threats using straightforward commands.
Related: Buy Ubuntu VPS in Canada
Installing UFW on Ubuntu
Embarking on your quest to make your Ubuntu server guarded starts with installing UFW. UFW comes pre-packed with most installations, so you probably already have it installed on your Ubuntu system. But there’s no harm in double checking if you have it or installing the latest version. It’s as straightforward as executing a few commands in your terminal.
Let’s make sure your system’s package index is up to date:
sudo apt updateThis command updates your package list to make sure that all subsequent installations grab the latest versions available.
Next, to install UFW, just type:
sudo apt install ufwYour system might require your confirmation. Proceed by pressing Y for yes to give it the green light. Shortly, UFW will be nestled into your system.
But installation is only the beginning. Before we start shaping the rules, it is very important to check if UFW is active. Run:
sudo ufw status verboseIf it’s inactive, the message “Status: inactive” will be displayed. But worry not, awakening this sleeping sentinel is but a single command away:
sudo ufw enable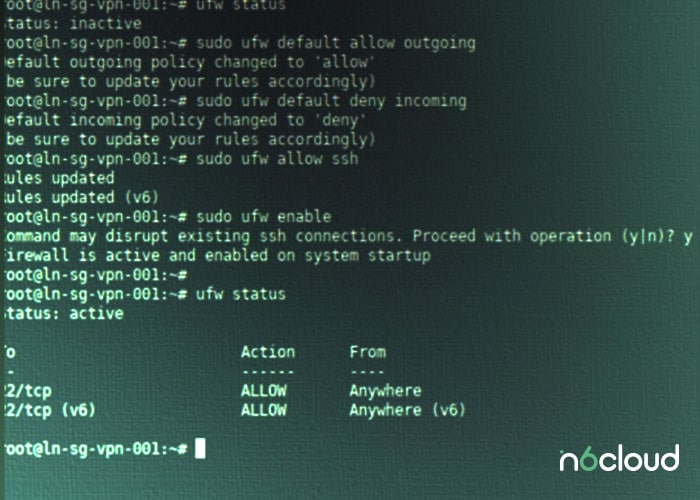
This will prompt UFW to rise and shine, ready to defend your system. Upon enabling it, you’ll see “Status: active” if you rerun the status command, confirming that UFW is actively guarding your system.
Once the UFW is installed and active, you’ve laid the foundation for a secure system. Remember, a firewall only works effectively if running, so checking the status should become an instinctive practice to you as an administrator.
Configuring UFW Rules
Once the UFW is activated, you’ll have to shape your firewall’s policy—the rules that determine traffic flow in and out of your server. It is kind of like training your guard dog to know who’s a friend and a foe. You don’t need to know intricate command syntax; UFW simplifies this with intuitive commands.
Begin by setting the ground rules. It’s wise to adopt a ‘deny by default’ approach, allowing only specific traffic to pass. Set your default policies with:
sudo ufw default deny incomingsudo ufw default allow outgoingThese commands block all incoming traffic; in the meanwhile, they ensure that your server can still communicate outwardly—a good setup for most servers.
Now, let’s open the doors for essential services. If you’re running a web server, you’ll need to allow HTTP traffic:
sudo ufw allow httpOr you might be hosting a secure HTTPS site:
sudo ufw allow httpsNeed to access your server remotely through SSH? Then you must keep that port open:
sudo ufw allow sshAnd there you have it—now your server is successfully configured to allow web traffic and remote administration.
If you ever need to retract a rule, for instance, if you decide to close SSH access, simply replace allow with deny:
sudo ufw deny sshBut rules aren’t just limited to services; you can get specific. Say you want to allow traffic from a particular IP address, you can do that too:
sudo ufw allow from 192.168.1.5This command allows all traffic from the IP address 192.168.1.5.
Managing UFW requires constant effort and attention. As your server’s role evolves, your rules should be adjusted accordingly. To remove a rule, you can use the delete command, followed by the original rule:
sudo ufw delete allow httpTo see all the rules you’ve set, simply type:
sudo ufw status numberedThis command provides a numbered list of all your active rules and makes tracking or removing specific ones easy.
Related: How to Install PostgreSQL in Linux VPS
Advanced UFW Features
Diving deeper into UFW’s capabilities, let’s explore advanced features that give you more granular control over your server’s network traffic. This is where UFW truly showcases its powers, allowing for intricate rule configurations that cater to more complex scenarios.
Imagine you’re hosting multiple services on your server and need to determine traffic rules for different ports. UFW makes this easy. If you have a custom application running on port 5000, you can open it up with:
sudo ufw allow 5000Or you might want to restrict this port to TCP traffic only for added security:
sudo ufw allow 5000/tcpNow, let’s take into account the scenario that you have a range of ports to manage, such as those used by a specific application suite. UFW can handle ranges as well:
sudo ufw allow 6000:6007/tcpThe command above opens all TCP ports from 6000 to 6007, inclusive.
Advanced rule definition also includes specifying source IPs. If you wish to restrict connections to a service from a specific IP range, UFW has got your back:
sudo ufw allow from 192.168.1.0/24 to any port 22This rule allows SSH connections (port 22) from any device with an IP address within 192.168.1.0/24 IP prefix.
UFW’s proficiency is wider than IPv4. In an internet landscape that’s gradually shifting to IPv6, UFW is fully capable. By default, it automatically configures both IPv4 and IPv6 settings and makes sure that your firewall is future-proof.
Another power feature is setting up rules for applications. Ubuntu includes several pre-configured profiles for common applications. To see the available application profiles, simply type:
sudo ufw app listYou might see entries like ‘Apache,’ ‘OpenSSH,’ or ‘Nginx Full.’ To allow traffic for an application profile, use:
sudo ufw allow 'Nginx HTTP'This is especially beneficial because it applies the essential rules for that application without requiring you to know the specific ports it uses.
Managing UFW Logs
Monitoring and understanding your firewall logs can make a clear distinction between a secure and exposed server. UFW’s logging capability makes sure that you’re always aware of the traffic it’s handling. It’s like having a surveillance system which records the comings and goings and provides invaluable assistance for spotting potential security threats or troubleshooting issues.
By default, UFW is configured to log firewall activity at a low level. Nevertheless, it is easy to adjust the logging level when more detailed information is needed. For instance, to set the logging to a medium level, which includes new connections, you would use:
sudo ufw logging mediumConversely, if the logs are too verbose, you can dial it back down:
sudo ufw logging lowRemember that excessive logging can quickly consume disk space and make log files unwieldy. Capturing the necessary information without being overwhelmed is a balancing act.
UFW logs its activity to the system log files. To find these logs, you can inspect with:
grep UFW /var/log/syslogTo enhance your real-time monitoring experience, you can use tail to follow the logs:
sudo tail -f /var/log/syslog | grep UFWThis command keeps the log file open and displays new log entries as UFW adds them. This feature is useful for observing your firewall’s performance live.
The next step is to interpret the logs. A UFW log entry typically includes the date, time, and the server’s hostname, followed by UFW, the action (ALLOW or BLOCK), and the specifics of the packet, such as the source and destination IP addresses, the port number, and the protocol.
When reviewing logs, look for unusual patterns, like multiple login attempts from unfamiliar IP addresses or blocked traffic to ports that shouldn’t be publicly accessible. These could be signs of a brute-force attack or a misconfigured rule that require immediate action.
Those who require an even more sophisticated approach to log management should consider integrating UFW with a log analysis tool. Using these tools helps parse, visualize, and alert based on log data, turning the arcane text of logs into actionable insights.
Conclusion
In closing, it’s clear that UFW is a vigilant gatekeeper for your Ubuntu server. UFW bringing simplicity and power into network security, and offers a user-friendly interface to the often complex iptables. By following the steps and best practices outlined, you’re able to configure, manage, and integrate UFW into your server’s defense strategy.
The key takeaway is that while UFW itself is a robust firewall management tool, its true strength lies in its ability to work in compliance with a suite of other security tools. From Fail2Ban’s proactive banishment of intruders to Logwatch’s insightful summaries and ClamAV’s vigilant malware scanning, your security apparatus is now multifaceted and resilient.
But the journey does not conclude here. The cybersecurity landscape is constantly evolving, with new threats and best practices emerging. Staying educated on the latest developments, maintaining your server, and regularly reviewing your security measures are all critical tasks for any administrator.
Embrace UFW not just as a tool but as a commitment to your network’s ongoing security and integrity. Whether you’re a novice user or a seasoned sysadmin, UFW is your steadfast ally. And keep in mind that the most robust firewall is not just built with good software—it’s built with the vigilance and wisdom of its keeper.



